
>>jRAT, also known as Jacksbot, is a RAT with history, written in Java. It has support for macOS, Linux, Windows, and various BSD. It also has the functionality to participate in DDoS-attacks as well as to perform click fraud. Note that the Adwind family often is mistakenly labeled as jRAT, because of a red herring reference to jrat.io.
>>jRAT is the cross-platform remote administration tool which is coded in the Java Since if it’s coded in Java it yields jRAT possibilities to run on all operation systems, Which includes Windows, Mac OSX, and Linux distributions. jRAT acquired recognition back in 2013 – 2014 when a jRAT server massively hit banks and their users in the center east, and it’s developed in Java and works on many operating programs like Linux, Home Windows, Mac, and so on. and I have examined this nice RAT it’s secure, quick, and Undetectable.However, now it’s not free.
================================================
- - - - - - - - - - - - Download Option - - - - - - - - - - - -
================================================
 |
| jRat v5 |
 |
| jRat Full Setup |
================================================
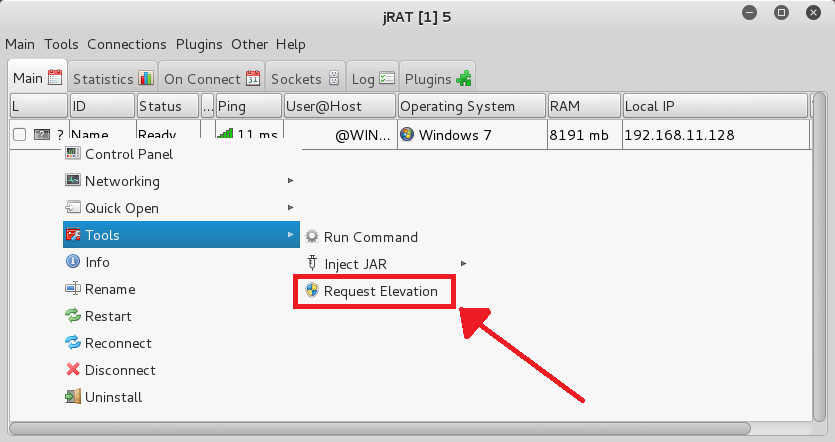
- - - - - - - - - - - - ScreenShot - - - - - - - - - - - -
================================================

================================================
- - How To Install JRAT Into (PC / Computer / Laptop) - -
================================================
- >> Unzip The Zip File Using Winrar
- >> After Extracting Install JRAT Setup File And Open
- Done
Note: Don't Update This Software - Update Only http://Dhsagarinfo.blogspot.com
================================================
- - - - - - - - - - - - Features - - - - - - - - - - - -
================================================
- Remote into the victim's desktop or active window
- See the victim's IP, full computer name, full username, OS, install date, and country
- Remotely execute a file from disk or URL
- Manipulate files
- Open a remote shell, allowing the attacker to use the command line
- Open a process manager to kill processes
- Manipulate the system registry
- Record the computer's camera and microphone
- Log keystrokes
- Steal passwords stored in browsers or in other applications
- And More And More Features. . .
================================================
https://DHSagarInfo.Blogspot.Com/
================================================



![[ FREE DOWNLOAD ] JSpy 0.3.1 And Cracked Version Portable (RAT) Remote Administration Tools / Remote Access Trojan BY DHS OFFICE](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEj33Vln92elgE6zRaWLd8p0nZ8uW23o01eDOgeX2izWYiSl_4G9AjGz43Fel2Q-LSYol0YFJyFhgkdhPqh86GLOJxmMXy25_rkk6IRiiqZfuLLfNC5i9JZiILiH6JGS_af5pTWDeaTYFK5E/s72-c/download-button+%25281%2529.gif)
![[ FREE DOWNLOAD ] DarkComet 5.3.1 And [ Complete Crack Setup ] Portable (RAT) Remote Administration Tools / Remote Access Trojan BY DHS OFFICE](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgFtDfetT3jfPs8efyHZhNgXoGLJtjgqm2hCnkAG55OrgP_UhNvyjIekquehR2Z4WKQRzMVc5A3v6YAg2JyNlRYntjNy6VkAIpuVRI89qZEXsfbyKqeg7yfAnFylFG1gOF72fgaqtCdmPo7/s72-c/1.png)
![[ FREE DOWNLOAD ] Plasma RAT - Cracked Portable (RAT) Remote Administration Tools / Remote Access Trojan BY DHS OFFICE](https://4.bp.blogspot.com/-6UPEpmq1kd0/V1WLDIo9p1I/AAAAAAAAW6U/a4Ge4ieUTgM-MVXsLAwND2XAfFgtbDOaACLcB/s72-c/Plasma%2B1.7%2BLatest%2BEdition.png)
No comments:
Post a Comment
Submit Your Comment, I Am Reply After Some Time Later. . .